Q.1 Mapping of Computer hardware
| SerNo. | Hardware resource | Resources in kitchen of a restaurant |
|---|---|---|
| 1 | CPU of the computer | (a) Countertop |
| 2 | Main Memory or RAM | (b) Cupboard |
| 3 | Disk | (c) Chef at the restaurant |
1-c,2-b,3-a
1-c,2-a,3-b
1-b,2-a,3-c
1-a,2-b,3-c
Q.2 Which command is used to print the current working directory?
cd
ls
pwd
None of above
Q.2 Composition of Operating System
According to you, what is an operating system made of?
Collection of hardware components
Collection of input-output devices
All the above
Collection of software functions
Q.3 Code Sharing by OS
OS acts as a resource manager
OS hides the hardware complexity
OS acts as an interface between applications and hardware
OS makes it easier for user to use the hardware.
Q.4 Example: A user using different vendors of speakers on the same computer system.
Arbitration
Abstraction as well as arbitration
Abstraction
None of above
Q.5 Example: Interchangeable access to hard disk and SSD disk.
Arbitration
Abstraction as well as arbitration
Abstraction
None of above
Q.6 Which command is used to print the current working directory?
Arbitration
Abstraction as well as arbitration
Abstraction
None of above
Q.7 Which of the following choices best describes the functions of an operating system?
To allow people to use the computer
To keep system programmers employed
To make the most efficient use of computer hardware
To make it difficult for layman users to damage the computer system
Q.8 Which of the following are the parts of the kernel of an operating system:
File Editor
Cache Memory
File Manager
I/O manager
Process manager
Web browser
Q.9 Kernel Functionalities
| SerNo. | Task | Functionalities |
|---|---|---|
| 1 | Reading the contents of a file | (a) Memory Management |
| 2 | Copying the file contents into the memory | (b) Process Management |
| 3 | Whole process of copying and pasting the contents of file | (c) File Management |
1-a,2-b,3-c
1-b,2-c,3-a
1-c,2-a,3-b
1-b,2-a,3-c
Q.10 System calls are invoked by using:
Polling
An indirect jump
A software interrupt
A privileged instruction
Q.11 Match the following for system calls listed in List-1 with appropriate functions in List-2:
| SerNo. | List-1 | List-2 |
|---|---|---|
| 1 | exec() | (a) Creates a new process |
| 2 | exit() | (b) Keeps the process id same and replaces the running code with a new code |
| 3 | wait() | (c)Terminates a running process properly |
| 4 | fork() | (d)A process synchronizes with termination of child process |
(a)-3,(b)-2,(c)-4,(d)-1
(a)-2,(b)-3,(c)-4,(d)-1
(a)-2,(b)-3,(c)-4,(d)-1
(a)-2,(b)-4,(c)-3,(d)-1
Q.12 Commands Exploration
| SerNo. | Bracket-1 | Bracket-2 |
|---|---|---|
| 1 | kill-3851 | (a) Passes a keyboard interrupt to the running process |
| 2 | kill-93851 | (b) Abruptly terminates the running process |
| 3 | kill-23851 | (c)Properly terminates the running process |
| 4 | kill-I | (d) Lists all the available signals that can be passed to kill command |
1 - c, 2 - d, 3 - a, 4 - b
1 - a, 2 - b, 3 - c, 4 - d
1 - c, 2 - b, 3 - a, 4 - d
1 - c, 2 - a, 3 - b, 4 - d
Q.13 Choose the correct statements in relation to system calls and commands of the terminal?
Operating systems are mostly implemented in C. System calls are function calls to implementations of functions where they interact with hardware resources.
Terminal commands are a wrapper over the system calls. Behind the scenes of terminal commands are function calls to the system calls.
System calls are used to interact with the kernel of Operating systems.
All the above statements are correct.
Q.14 Commands Exploration
| SerNo. | Bracket-1 | Bracket-2 |
|---|---|---|
| 1 | cat newfile.txt | (a) It will append the contents of one file to another |
| 2 | cat newfile.txt anotherfile.txt | (b) It will show content of a file with line number |
| 3 | cat -n newfile.txt | (c)It will show the contents of both newfile.txt and anotherfile.t |
| 4 | cat newfile.txt >> anotherfile.txt | (d)It will show the contents of newfile.txt |
1 - a, 2 - c, 3 - b, 4 - d
1 - d, 2 - b, 3 - c, 4 - a
1 - d, 2 - c, 3 - b, 4 - a
1 - a, 2 - b, 3 - c, 4 - d
Q.15 Select the correct definition for abstraction, mechanism and policies
Abstraction includes OS’s abstracted form of application as well as hardware resources, mechanism is how to do something and policies are what will be done
Abstraction includes OS’s abstracted form of hardware resources, mechanism is what will be done and policies are how to do something
Abstraction includes OS’s abstracted form of hardware resources, mechanism is how to do something and policies are what will be done
Abstraction includes OS’s abstracted form of application as well as hardware resources, mechanism is what will be done and policies are how to do something
Q.16 Applications have programs [instructions] and data that are not useful, as they remain passive and
don't complete any tasks. OS converts them into process and makes it useful. Select the correct statements
about a process.
A. Process is program under execution
B. Process can be termed as an active entity and programs can be termed as passive entity
only A is correct
only B is correct
Both A and B are correct
Both are in correct
Q.17 Which of the following descriptions is closest and most accurate description for virtualization of CPU?
OS switches the CPU between different processes.
OS creates processes from the programs and data stored in disk.
OS runs multiple applications on a CPU and this creates the illusion that we are using multiple CPUs.
None.
Q.18 CPU Utilization
30%
60%
70%
75%
Q.19 How OS creates a process
3,4,2,1,5
3,4,1,2,5
3,2,4,1,5
,1,2,3,4,5
Q.20 View of Allocated Memory of Process
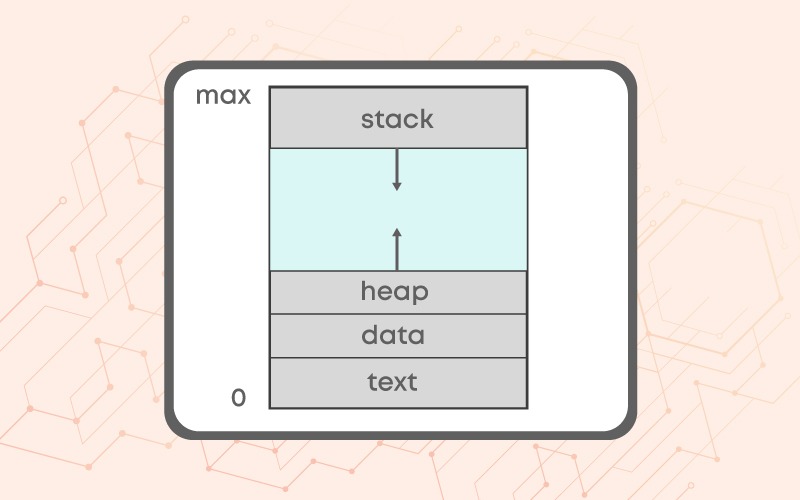
1 - a, 2 - b, 3 - c, 4 - d
1 - b, 2 - d, 3 - c, 4 - a
1 - b, 2 - c, 3 - d, 4 - a
1 - a, 2 - c, 3 - d, 4 - b
Q.21 Errors During Process Execution

P = Memory Insufficient Error, Q = Stack Overflow Error
P = Illegal Memory Referencing Error, Q = Memory Insufficient Error
P = Stack Overflow Error, Q = Memory Insufficient Error
P = Memory Insufficient Error, Q = Illegal Memory Referencing Error
Q.22 Which is the correct description about Process Control Block?
Process type variable
A block of space in disk for each application
Per process data structure
A block in memory for each application
Q.23 Order of Instruction Execution
1. Increment the Program counter
2. Fetch the instruction from the address in the Program Counter
3. Execute the instruction
Select the correct order these steps.
2,3,1
3,1,2
2,1,3
1,2,3
Q.24 State Transitions
I. A running process can move to ready state.
II. A ready process can move to running state.
III. A blocked process can move to running state.
IV. A blocked process can move to ready state.
Which of the above statements are TRUE ?
I, II, and III only
II and III only
I, II, and IV only
I, II, III and IV only
Q.25 The state of a process after it encounters an I/O instruction is?
Ready
Idle
Blocked
Running
Q.26 Process is in a ready state _______ .
when process is using the CPU
when process is scheduled to run after some execution
None of above
Q.27 The processes that are residing in main memory and are ready and waiting to execute are kept on a list called _____________
job queue
execution queue
ready queue
process queue
Q.28 Process Transitions
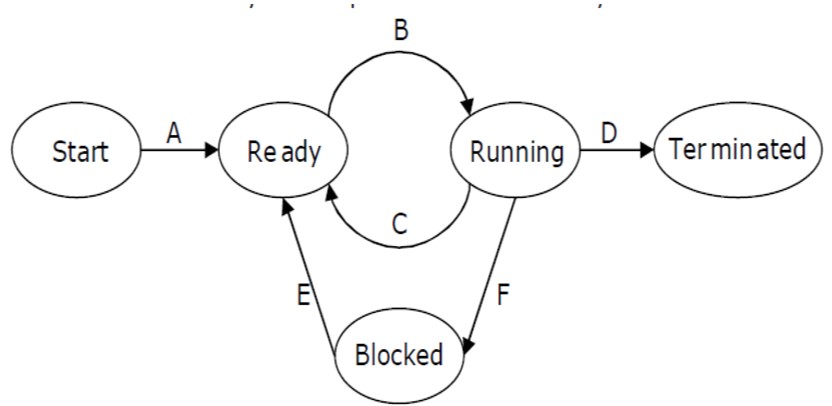
I and II
I and III
II and III
II and IV
Q.29 Choose the correct option
| SerNo. | List-1 | List-2 |
|---|---|---|
| A | Moves suspended process to secondary storage | (I) Short term scheduler |
| B | Loads the process into memory for execution | (II) Long term scheduler |
| C | Moves one of the processes to running state | (III) Medium Term Scheduler |
A - I, B - II, C - III
A - II, B - I, C - III
A - III, B - II, C - I
A - I, B - III, C - II
Q.30 If you are performing a "state save" on the current process and a "state restore" on a different process, while switching the CPU from one process to another is called ________
State Switch
Process State Change
Context Switch
PCB Change
Q.31 Select the correct statements about context switching.
A. Context switching gives you the ability to do multiprogramming
B. Context switching only happens when the current process has to do I/O operation.
Only B
Both are correct
Only A
Neither A nor B is correct
Q.32 Which of the following statements are correct, if a parent process creates a new child process?
i. Both the processes have ppid associated with them.
ii. Both parent process and child process have different process ids.
Only i
Only ii
Both i and ii
None of these
Q.33 We have already discussed the reasons for which a process may get terminated. Now, think and select which of the following is/ are legitimate reasons due to which a process may terminate one of its child processes?
The child process is taking more resources than allocated.
The task assigned to the child process is no longer required.
All the above
The parent process is terminating, and the OS does not allow a child to continue if its parent exits
Q.34 Commands Exploration
| SerNo. | Bracket-1 | Bracket-2 |
|---|---|---|
| 1 | grep -c "linux" cnfile.txt | (a) Displays only the matched pattern |
| 2 | grep -l "linux" * | (b) Checks the complete words in a file |
| 3 | grep -w "linux" cnfile.txt | (c) Displays the file names that matches the pattern |
| 4 | grep -o "linux" cnfile.txt | (d) Displays the count of number of matches |
1 - a, 2 - c, 3 - b, 4 - d
1 - d, 2 - b, 3 - c, 4 - a
1 - d, 2 - c, 3 - b, 4 - a
1 - a, 2 - b, 3 - c, 4 - d
Q.35 Terms and Description
The reasons for desirable processes included terms such as turnaround time, wait time and response time. In the following table, column 1 contains terms and column 2 contains its description. Match the terms to their appropriate description.| SerNo. | Terms | Description |
|---|---|---|
| 1 | Turn around time | (a) The time duration between process getting into ready queue and process getting CPU for the first time. |
| 2 | Wait time | (b) The time process spends waiting for the CPU. |
| 3 | Response time | (c) The time duration between the terminated state and ready state [this is taken from the first time process enters the ready state] |
1 - c, 2 - a, 3 - b
1 - b, 2 - c, 3 - a
1 - c, 2 - b, 3 - a
1 - a, 2 - b, 3 - c
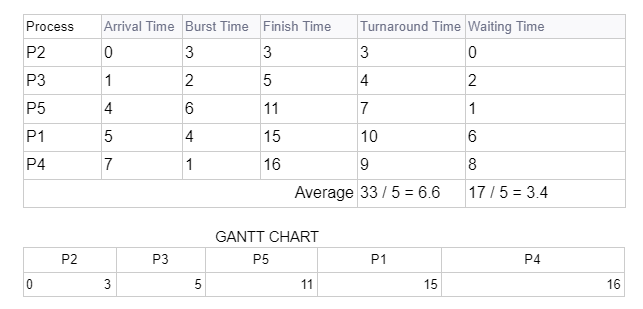
Q.36 Scheduling Processes: Problem 1
Consider the set of 5 processes whose arrival time and burst time are given below. What is the average turnaround time and average waiting time if the scheduling algorithm used is First Come First Served (FCFS) scheduling?| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 5 | 4 |
| P2 | 0 | 3 |
| P3 | 1 | 2 |
| P4 | 7 | 1 |
| P5 | 4 | 6 |
Turnaround time: 7.2 units, Waiting time: 4.3 units
Turnaround time: 5.1 units, Waiting time: 3.1 units
Turnaround time: 6.6 units, Waiting time: 3.4 units
Turnaround time: 6.9 units, Waiting time: 5.1 units
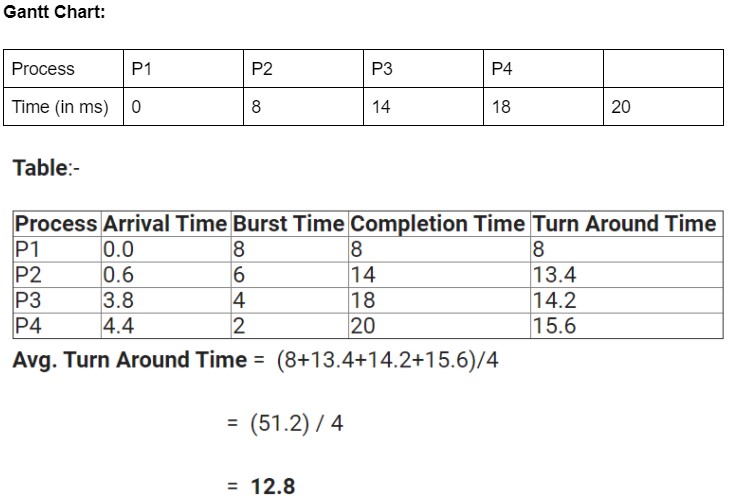
Q.37 Scheduling Processes: Problem 2
Consider the following four processes with their corresponding arrival time and burst time:| Process ID | Arrival Time | Burst Time(in ms) |
|---|---|---|
| P1 | 0 | 8 |
| P2 | 0.6 | 6 |
| P3 | 3.8 | 4 |
| P4 | 4.4 | 2 |
15
13
12.8
None of above
Q.38 What is the Convoy Effect?
Convoy Effect is a situation where many processes, who need to use a resource for a short time, are blocked by one process holding that resource for a long time. This essentially leads to poor utilization of resources and hence poor performance.
Q.39 Scheduling Processes: Problem 3
Consider the following set of processes with their arrival times and burst time (in milliseconds) as given below. If the Operating System uses Shortest Job First Scheduling algorithm, what is the average waiting time of the processes?| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 7 |
| P2 | 3 | 5 |
| P3 | 5 | 11 |
| P4 | 10 | 4 |
4.90 milliseconds
2.35 milliseconds
4.25 milliseconds
5.72 milliseconds
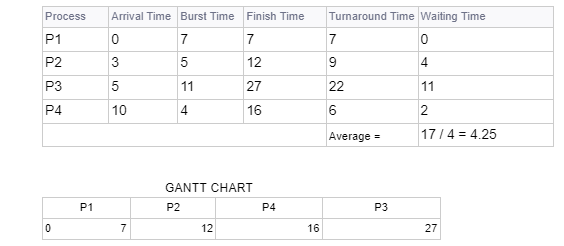
Q.40 Preemptive Scheduling
Consider the following scenarios with respect to CPU scheduling decisions:i. A process switches from running state to waiting state
ii. A process switches from the running state to the ready state
iii. A process switches from the waiting state to the ready state.
iv. A process terminates.
A Preemptive Scheduling can take place among which of the following scenarios?
i and iv
i and iii
ii and iii
i and ii
41 Non Preemptive Scheduling
Consider the following scenarios with respect to CPU scheduling decisions:i. A process switches from running state to waiting state
ii. A process switches from the running state to the ready state
iii. A process switches from the waiting state to the ready state.
iv. A process terminates.
A Non Preemptive Scheduling can take place among which of the following scenarios?
ii and iii
i and iii
i and iv
i and ii
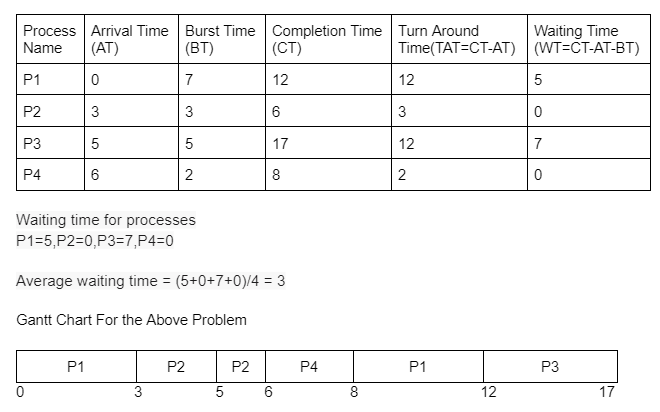
Q.42 Scheduling Processes: Problem 4
Consider the following CPU processes with arrival times (in milliseconds) and length of CPU bursts (in milliseconds) as given below:| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 7 |
| P2 | 3 | 3 |
| P3 | 5 | 5 |
| P4 | 6 | 2 |
5
4
3
6
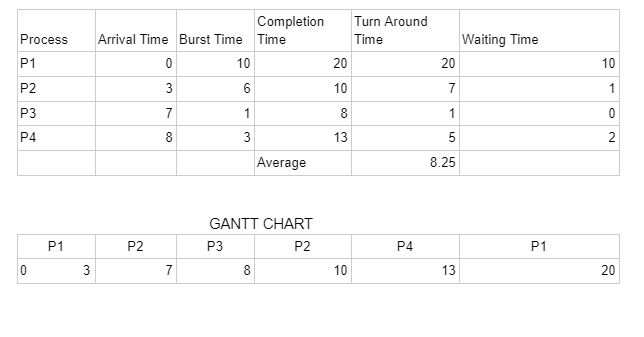
Q.43 Scheduling Processes: Problem 5
Consider the following processes, with the arrival time and the length of the CPU burst given in milliseconds. The scheduling algorithm used is preemptive shortest job first.| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 10 |
| P2 | 3 | 6 |
| P3 | 7 | 1 |
| P4 | 8 | 3 |
8.26
8.27
8.25
8.28
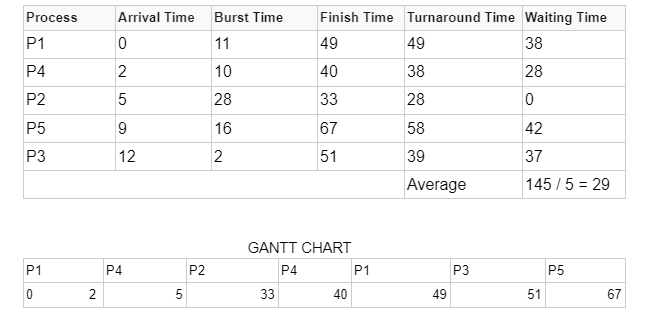
Q.44 Scheduling Processes: Problem 6
Consider the set of processes with arrival time(in milliseconds), CPU burst time (in milliseconds), and priority(0 is the highest priority) shown below. None of the processes have I/O burst time.| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 10 |
| P2 | 3 | 6 |
| P3 | 7 | 1 |
| P4 | 8 | 3 |
32
31
29
30
Q.45 FCFS Scheduling
The arrival times and burst times for a set of 5 processes are given below. If First Come First Served (FCFS) scheduling algorithm is followed, and there is 2 units of overhead in the scheduling the processes, then what is the efficiency of the algorithm?| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 5 |
| P2 | 1 | 4 |
| P3 | 2 | 2 |
| P4 | 3 | 7 |
81.2%
72.3%
67.7%
71.4%
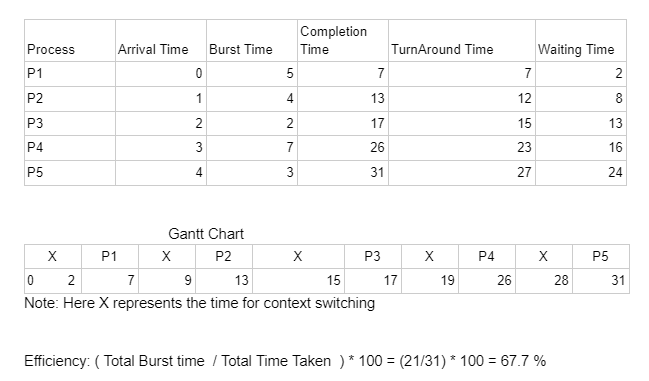
Q.46 Find average waiting time
Consider the following four processes with arrival times (in milliseconds) and their length of CPU bursts (in milliseconds) as shown below:| Process ID | P1 | P2 | P3 | P4 |
|---|---|---|---|---|
| Arrival Time | 0 | 1 | 3 | 4 |
| CPU burst time | 3 | 1 | 3 | z |
2
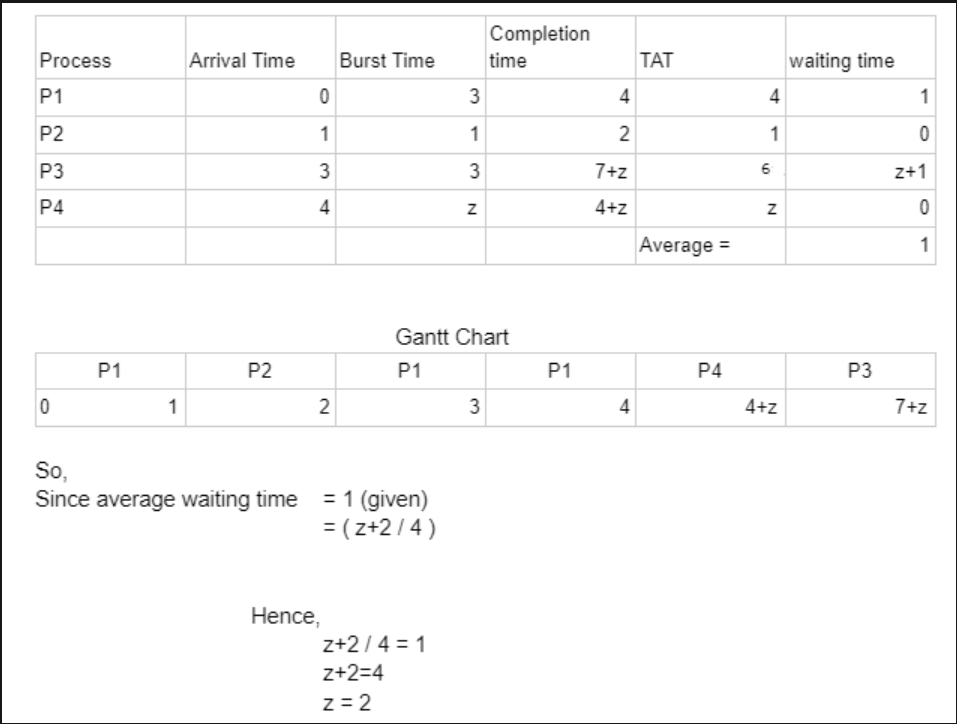
Q.47 Preemptive Shortest Remaining Time First Scheduling
Consider the following set of processes with their arrival times and burst time (in milliseconds) as given below. If the Operating System uses Preemptive Shortest Job First Scheduling algorithm, then what is the average turnaround time of the processes?| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 11 |
| P2 | 4 | 8 |
| P3 | 6 | 2 |
| P4 | 9 | 4 |
9.2 milliseconds
10 milliseconds
11 milliseconds
8.3 milliseconds
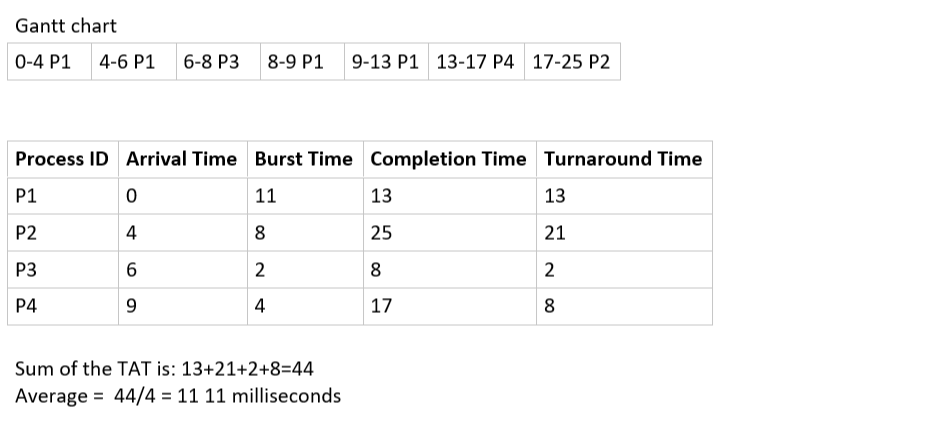
Q.48 Preemptive Priority Scheduling
Consider the following set of processes with their arrival times and burst time (in milliseconds)and priority (0 is the highest priority) as given below. None of the processes have I/O burst time. If the Operating System uses Preemptive Priority Scheduling algorithm, what is the average waiting time of the processes?| Process ID | Arrival Time | Burst Time | Priority |
|---|---|---|---|
| P1 | 0 | 10 | 2 |
| P2 | 4 | 19 | 1 |
| P3 | 10 | 1 | 3 |
| P4 | 3 | 9 | 0 |
15 milliseconds
14 milliseconds
16 milliseconds
13 milliseconds
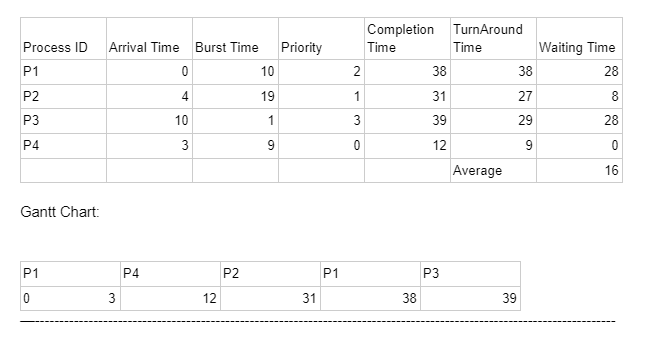
Q.49 Non Preemptive Priority Scheduling
Consider the following set of processes with their arrival times and burst time (in milliseconds)and priority (higher number means higher priority) as given below. None of the processes have I/O burst time. If the Operating System uses Non Preemptive Priority Scheduling algorithm, then what is the average turnaround time and average waiting time of the processes?| Process ID | Arrival Time | Burst Time | Priority |
|---|---|---|---|
| P1 | 0 | 5 | 1 |
| P2 | 1 | 7 | 3 |
| P3 | 2 | 3 | 2 |
| P4 | 3 | 4 | 4 |
Turnaround time: 12.32 milliseconds, Waiting time: 7 milliseconds
Turnaround time: 11.56 milliseconds, Waiting time: 7 milliseconds
Turnaround time: 10.75 milliseconds, Waiting time: 6 milliseconds
Turnaround time: 13.43 milliseconds, Waiting time: 6 milliseconds
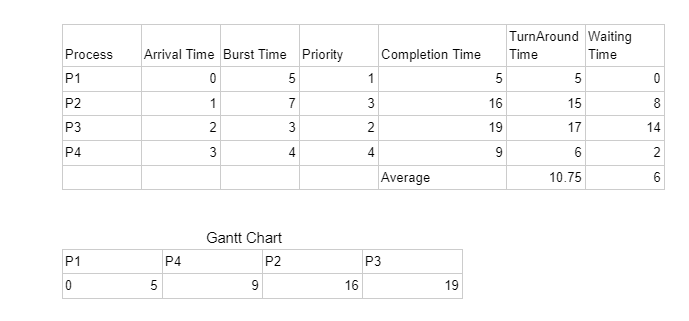
Q.50 Round Robin Scheduling Process
Consider the following set of processes, assumed to have arrived at time 0. Consider the CPU scheduling algorithms Shortest Job First (SJF) and Round Robin (RR). For RR, assume that the processes are scheduled in the order: P1, P2, P3, P4.| Process ID | Burst Time |
|---|---|
| P1 | 8 |
| P2 | 7 |
| P3 | 2 |
| P4 | 4 |
4.25
5.50
5.25
6.25
Q.51 Choose the correct option
Which of the following statements are TRUE for Multilevel Queue Scheduling?1. The main disadvantage of Multilevel Queue Scheduling is the problem of starvation for lower-level processes.
2. With the help of this scheduling we can apply various kind of scheduling for different kind of processes.
3. There are three types of processes and each set of processes can have a different scheduling algorithm. Example of scheduling: For System Processes: First Come First Serve(FCFS) Scheduling, For Interactive Processes: Shortest Job First (SJF) Scheduling, For Batch Processes: Round Robin(RR) Scheduling
1 and 2 are correct
2 and 3 are correct
All the statements are correct
1 and 3 are correct
Q.52 Choose the correct option
Which of the following statements are TRUE for Multilevel Queue Scheduling and Multilevel Feedback Queue Scheduling?1. In the Multilevel queue (MLQ) processes are classified into different groups, whereas the Multilevel Feedback queue (MLFQ) contains two queues, lower-priority queues and higher priority queues.
2. In the Multilevel queue (MLQ), there is no possibility of starvation.
3. In the Multilevel queue (MLQ) the processes are permanently assigned to one queue, whereas the Multilevel Feedback queue (MLFQ) it allows a process to move between the queues.
1 and 2 are correct
2 and 3 are correct
1 and 3 are correct
All correct
Q.53 Which among the following is the simplest CPU scheduling algorithm by far?
Shortest Job First Scheduling
Priority Scheduling
First-Come, First-Served Scheduling
Round Robin Scheduling
Q.54 Round Robin Scheduling
Consider the following set of processes with their arrival times and burst time (in milliseconds) as given below. If the Operating System uses Round Robin Scheduling algorithm with time quantum=2 units, then what is the average turnaround time and average waiting time of the processes?| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 5 |
| P2 | 1 | 3 |
| P3 | 2 | 1 |
| P4 | 3 | 2 |
Turnaround time: 8.30 milliseconds, Waiting time: 5.40 milliseconds
Turnaround time: 6.37 milliseconds, Waiting time: 4.02 milliseconds
Turnaround time: 7.25 milliseconds, Waiting time: 4.50 milliseconds
Turnaround time: 7.02 milliseconds, Waiting time: 3.17 milliseconds
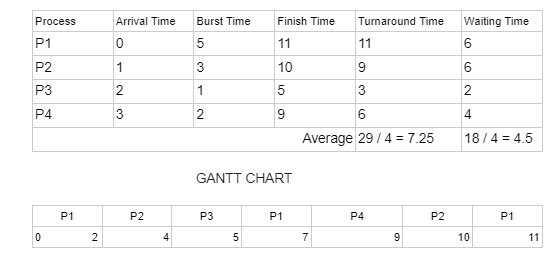
Q.55 Order of Completion
Consider the following set of processes, with arrival times and the required CPU-burst times given in milliseconds.| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 4 |
| P2 | 2 | 2 |
| P3 | 3 | 1 |
P1, P2, P3
P3, P2, P1
P2, P1, P3
P2, P3, P1
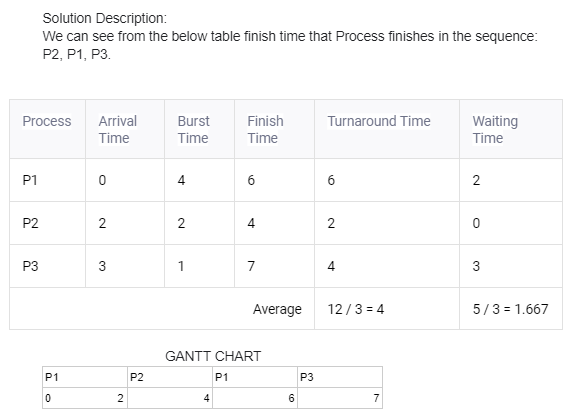
Q.56 Choose the correct option
For the processes listed in the following table, which of the following scheduling schemes will give the lowest average turnaround time?| Process ID | Arrival Time | Burst Time |
|---|---|---|
| P1 | 0 | 3 |
| P2 | 1 | 6 |
| P3 | 4 | 4 |
| P4 | 6 | 2 |
First Come First Serve
Non-preemptive Shortest Job First
Shortest Remaining Time
Round Robin with Quantum value two
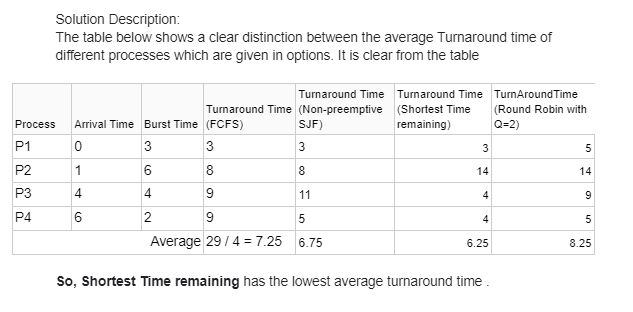
Q.57 Choose the correct option
Consider an arbitrary set of CPU-bound processes with unequal CPU burst lengths submitted at the same time to a computer system. Which one of the following process scheduling algorithms would minimize the average waiting time in the ready queue?Round-robin with time quantum less than the shortest CPU burst
Uniform random
Shortest remaining time first
Highest priority first with priority proportional to CPU burst length
Q.58 Scheduling of Multilevel Queues
How can multilevel queues be scheduled?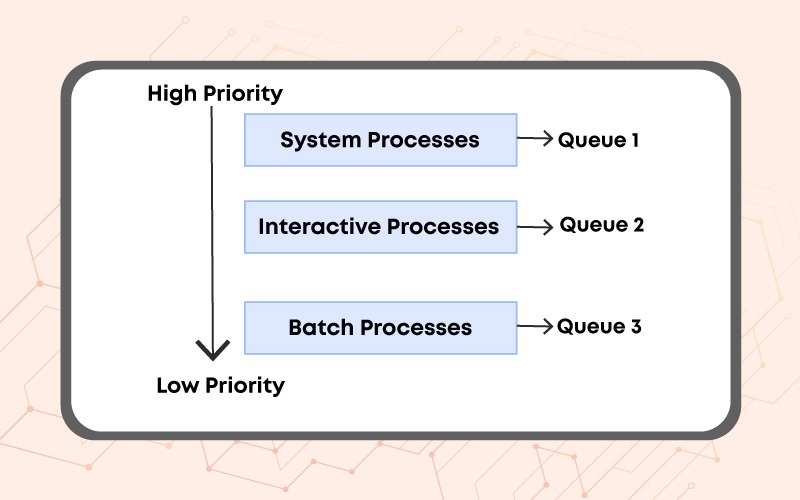
A multi-level queue scheduling algorithm partitions the ready queue into several separate queues. The processes are permanently assigned to one queue, generally based on some property of the process, such as memory size, process priority, or process type. Most importantly, each queue has its own scheduling algorithm.
Q.59 Parameters for MLFQ Scheduler
Which of the following parameters are required to define a multilevel feedback queue scheduler?The number of queues
The scheduling algorithm for each queue which can be different from FIFO
All of these
The method used to determine when to promote a process to a higher priority queue
Q.60 Problems in Time Sharing
“One way to implement time sharing will be to run one process for a certain period of time, giving it full access to all memory and related resources, then stop it, run state save on this process and store saved state to disk, load some other process’s state, run it for a while” Which of the following most accurately describes the problem with the above approach to implement time sharing?Saving and restoring register-level state (such as the program counter and general-purpose registers) is slow.
This approach may not work for processes requiring large amount of memory.
Saving the entire contents of memory to disk is extremely non-performant, as time taken to move the contents between these storage device is brutally slow. This makes this approach very slow.
There isn’t enough space for saving the entire state of processes so we may get insufficient memory error i.e. we may run out of memory.
Q.61 Function of OS
The act of hiding the actual physical address details of a process and showcasing only virtual address of the process's private address space is __________Example of arbitration function of OS
Example of OS acting as an interface between hardware and applications
Example of abstraction function of OS
None of the above
Q.62 Virtual Address Space
Which of the following is/are region(s) of the virtual address space that may grow or shrink, while the process is running?code, stack, heap
stack
stack, heap
code, stack
Q.63 Physical Address Mapping
Process P with 16KB of address space, loads into memory at the physical address of 256KB. When process P tries to perform a load at address 0KB (which we will call a virtual address), then the OS, with the help of hardware, maps this virtual address to which of the following physical address?Physical address 0KB
Physical address 320KB
Physical address 256KB
Physical address 512KB
Q.64 Select True or False for the following statement. Statement: The stack is used for dynamically-allocated data structures such as linked lists and many others. It is user-managed memory, such as that you might receive from a call to malloc() in C.
True
False
Q.65 Choose the correct option
Select the correct statements about stack and heap.1. Unlike a stack where the memory is allocated as a contiguous block, in the case of the heap, the memory is allocated in the random order.
2. Unlike stack memory, allocation and deallocation in heap memory have to be handled by the programmer.
3. For a particular function, stack memory is deallocated as soon as the return statement is executed.
4. If the programmer doesn’t manage the heap memory efficiently and forgets to deallocate the allocated memory, it will cause a memory leak.
1 and 2 are correct
2, 3 and 4 are correct
All the statements are correct
1, 2 and 3 are correct
Q.66 Layer of Memory
In the process of retrieving the data stored in memory, what are the reasons of adding an extra layer of virtual memory?This is done so that the process doesn’t have direct access to physical memory.
This is done for ease of usage of physical memory. Virtual memory makes it easier for the process to access physical memory.
This is done for protection. By adding this layer, the OS makes sure that processes are isolated and protected from one another.
None of above
Q.67 Base Register
Which of the following is achieved by using a base register?It stores the contents in the virtual address space so that they can be transferred to their corresponding physical address space.
It is used to store all the physical addresses that form the address space of a program.
It transforms virtual addresses (generated by the program) into physical addresses.
It ensures that such addresses are within the confines of the address space.
Q.68 Choose the correct option
What does a CPU do when a process tries to access memory outside its bounds?The CPU modifies its bounds to access the memory that the process wants.
The CPU omits that particular instruction in the program
The CPU raises an exception.
None of above
Q.69 Protection of Processes
Which of the following address is, generated by computer system, to isolate and protect the processes from each other?Note: This question was asked in Amazon.
Physical Address
Absolute Address
Virtual Address [also known as logical address]
None of above
Q.70 Address Mapping
Runtime mapping from virtual to physical address is done by -Note: This question was asked in TCS.
CPU
Operating System
Memory Management Unit
None of above
Q.71 Problems of Fixed Partitioning
Select the correct statement about problems faced in Fixed Partitioning:The problem of Internal fragmentation is present in the Fixed Partitioning.
The degree of multiprogramming is fixed in Fixed Partitioning.
All the above statements are correct.
A process whose size is greater than the largest contiguous space available cannot be accommodated.
The problem of External fragmentation is present in the Fixed Partitioning.
Q.72 Identify the Allocation Method
Identify the memory allocation method applied in the following diagram:
It can be both. Insufficient data.
Dynamic Partitioning Method
Fixed Partitioning Method
Neither Fixed Partitioning nor Dynamic Partitioning
Q.73 Solutions from Dynamic Partitioning
Select the problems of Fixed Partitioning, which are solved by Dynamic Partitioning:1. Problem of Internal Fragmentation
2. Fixed degree of multiprogramming
3. Problem of External Fragmentation
2 and 3 are solved
1 and 3 are solved
1 and 2 are solved
1, 2 and 3 are solved
Q.74 Free Space in Memory
The free space consists of variable-sized units such that there is not enough contiguous space to satisfy a request or to allocate to a process.For example: in the following, even if we have free space of 5 MB, we will not be able to allocate that space to a process which comes with a request for 5 MB because 5 MB is not present contiguously.
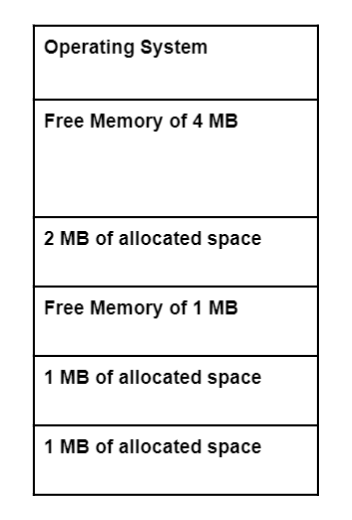 Which of the following best describes the statement above?
Which of the following best describes the statement above?
Partitioning
Internal Fragmentation
External Fragmentation
None of the above
Q.75 Which of these data structure was used to represent free memory in the lecture video? ?
free hash table
free tree
free list
free heap
Q.76 Time of Completion
In a computer system with 4 CPUs available, where the 'best-fit' algorithm is used for allocating 'jobs' to memory partitions, the following situation was encountered:| Partition sizes in KB | 4k | 8k | 20k | 2k | |||
|---|---|---|---|---|---|---|---|
| Jobs | 2k | 14k | 3k | 6k | 10k | 20k | 2k |
| Times for Execution | 4 | 10 | 2 | 1 | 1 | 8 | 6 |
20 units of time
18 units of time
19 units of time
21 units of time
Q.77 Choose the correct option
Consider the requests from processes in given order 300K, 25K, 125K, and 50K. Let there be two blocks of memory available of size 150K followed by a block size 350K. Assume the memory allocation technique to be used is Dynamic Partitioning. Which of the following partition allocation schemes can satisfy the above requests?Best fit but not first fit.
Both First fit & Best fit.
First fit but not best fit.
Neither first fit nor best fit.
Q.78 Best Strategy
Select all the basic strategies to manage free space in which we can avoid exhaustive searches on the entire free space:Best Fit
Worst Fit
First Fit
Next Fit
1. The First Fit algorithm scans the memory blocks, and whenever it finds the first big enough memory block to store a process, it stops scanning and loads the job into that block. This algorithm avoids exhaustive searches on entire free space.2. The Next Fit algorithm works the same as the First Fit algorithm, except that Next fit scans the memory blocks from the block where it previously allocated a job. Like the first-fit algorithm, the next fit algorithm avoids exhaustive searches on the entire free space.
3. The Best Fit algorithm searches the whole set of memory blocks and tries to find out the smallest memory block possible in the list that can accommodate the size requirement of the process. The best-fit algorithm results in exhaustive searches of the entire memory space.
4. The Worst Fit algorithm scans the entire memory block every time and tries to find out the biggest block in the list, which can fulfil the requirement of the process. The worst-fit algorithm results in exhaustive searches of the entire memory space.
Q.79 Fill in the blanks: Using the approach of ____________ to improve memory allocation, if a particular application has one (or a few) popular-sized requests that it makes, we’ll keep a separate list just to manage objects of that size. All other requests are forwarded to a more general memory allocator.
Buddy allocation
Growing the Heap
Segregated Lists
Merging
Q.80 In the following problem description, consider holes as synonyms for free memory spaces.
Problem Description:
Consider allocation of memory to a new process. Assume that none of the existing holes in the memory will
exactly fit the process’s memory requirement. Hence, a new hole of smaller size will be created if allocation
is made in any of the existing holes. Which one of the following statements is TRUE ?
The hole created by the worst fit is always larger than the hole created by the first fit.
The hole created by the first fit is always larger than the hole created by the next fit.
The hole created by the best fit is never larger than the hole created by the first fit.
The hole created by the next fit is never larger than the hole created by best fit.
Q.81 What does base of a segment contain?
The capacity or size of segment
Stores the starting address of virtual address space of memory
Contains the starting address where process is loaded at physical memory
None of above
Q.82 Which of the following can cause a segmentation fault?
The data of segment bases are corrupted
A process requesting an address which exist absolutely fine.
A process accessing illegal address, which is beyond the bounds of address space assigned to process
A process accessing stack segment instead of heap segment
Q.83 What are the bits introduced, per segment, to implement code sharing in memory management module of OS?
Read-write bits
Reading bits
Protection bits
Permission bits
Q.84 Select the correct option for the following statement:
To find which code segment the virtual address belongs to, we would always need 2 bits.
False
Ture
Q.85 Select the correct option for the following statement:
External fragmentation is avoided when segmentation is used.
False
Ture
Q.86 Select all the components in which the virtual address generated by a process is initially broken into:
the offset within the page
page table entry (PTE)
the virtual page number (VPN)
physical frame number (PFN)
Q.87 Fill in the blank: A __________ stores virtual-to-physical address translations, thus letting the system know where each page of an address space actually resides in physical memory.
page table entry (PTE)
page framepage offset
page table
None of above
Q.88 Which of the following refers to the fixed-sized units that the physical memory is divided into?
Pages
Page Tables
Page Frames
Segments
Q.89 Virtual Address to Physical Address
For a process of 64 B virtual address and 128 B physical address and following page table:What will be the physical address for virtual address 37?
| Virtual Page Number | Physical Page Number |
|---|---|
| 0 | 3 |
| 1 | 7 |
| 2 | 5 |
| 3 | 2 |
75
89
85
95
Q.90 Select the correct option for the following statement:
External fragmentation is avoided when paging is used.
Ture
False
Q.91 Slow Paging!?
What is the most accurate description for slowness of Paging?Division of physical address space into frames
Extra space allocated for page table
Too many memory references to access the actual data stored
Division of virtual address space into pages
Q.92 Fill the blank cells in table
.png)
Q.93 “TLB is a hardware cache which stores the contents of a Page table. CPU always checks TLB first, before moving to the page table in case of page miss. If the memory reference is made for the first time in TLB, then it always results in Page Miss.” Select the correct option for the above statement.
Ture
False
Q.94 What is the most accurate description of TLB hit?
The TLB contains the mapping for the requested physical address
The TLB checks and confirms whether this virtual address is accessible
The TLB contains the mapping for the requested virtual address
None of above
Q.95 Which of the following addition is done to provide hardware support for sharing of TLB across context switching?
Valid bit
Protection bit
Address space identifier (ASID)
Permission bit
Q.96 What is the term used for using swap space for accessing a page, which is not present in physical memory?
Segmentation Fault
Page Miss
Page Fault
Swap Space Hit
Q.97 Page Fault
Consider the following page trace:4,3,2,1,4,3,5,4,3,2,1,5
Determine the number of page fault that would occur if FIFO Page Replacement Algorithm is used with number of frames for the job m=4 will be
9
12
10
8
Q.98 LRU - I
An LRU page Replacement is used with four page frames and eight pages. How many page faults will occur with reference string 0172237103 if the four frames are initially empty?4
5
6
7
Q.99 LRU - II
How many hits occur in LRU page replacement algorithm for the given reference string with four page frames7,0,1,2,0,3,4,0,3,2,0,1?
3
4
5
6
Q.100 Which of the following statements are TRUE?
Program and Process, both are stored in main memory and threads are part of process and are, therefore, stored in main memory itself.
A program can have many processes, a process can have many threads and similarly one thread can be associated with multiple processes.
Program is stored in secondary memory, Process is stored in main memory and threads are part of process and are stored in main memory itself.
A program can have many processes, a process can have many threads, but one thread can belong to exactly one process.
Q.101 We know that allocation of stack space is different in Process and Thread and there is one stack per thread. This implies that the number of stack spaces is equal to the number of threads in the process. Can we say the same for heap space as well?
No
Yes
Q.102 What are the reasons for which multithreading is preferred over multiprocessing?
To make optimal use of multiple CPUs
Avoid blocking due to I/O
To optimally utilize the memory
To keep CPU busy all the time
Q.103 Do you think that the advantages of multithreading will hold true for a system with a single CPU as well?
Yes
No
Q.104 Threads are always executed in the same order and they always give the same output.
True
False
Q.105 Distinct Values
The following two functions P1 and P2 that share a variable B with initial value of 2:P1(){
C = B - 1;
B = 2 * C;
}
P2(){
D = 2 * B;
B = D - 1;
}
The number of distinct values that B can possibly take after execution is _________.
3
Q.106 The primary reason for the problem of race condition is uncontrolled scheduling of threads. Do you think a similar issue would have come if we would have used processes in place of threads?
Yes
No
Q.107 One of the solutions suggested to overcome the problem of race condition is Mutual Exclusion. Mutual exclusion implies that ____________
If a process is executing in its critical section, then no other process must be executing in their critical sections
If a process is executing in its critical section, then other processes must be executing in their critical sections
If a process is executing in its critical section, then all the resources of the system must be blocked until it finishes execution
None of above
Q.108 Hardware and OS support
In the following code segment, we are using locks to solve the problem of race condition. On executing this code segment, it was concluded that race condition is resolved. We are using a function called LOCK.acquire() to apply locks.Code Segment:
def calculate_count(arg):
LOCK.acquire()
print("{}:begin".format(arg))
global COUNT
for _ in range(1000000):
COUNT = COUNT + 1
print("{}:ends".format(arg))
LOCK.release()
What do you think is happening behind the scenes of this function LOCK.acquire(). Do you think it is taking hardware support to implement locks on the critical section?
We have to use hardware and OS support. It is well established that a simple flag variable cannot help us bring mutual exclusion and even Peterson's solution is valid only for two threads. For multiple threads (greater than two), we have to rely on hardware and OS support.
None of above
Q.109 Locks and Race Condition
Paragraph: In the locks solution to race condition problem, if one of the threads acquires the lock and then it is preempted by the OS.Question on the paragraph:
1. What happens to the other threads?
2. How does acquiring a lock prevent other threads from entering into the critical section.
Select the correct statements that answer above mentioned questions.
The other threads execute the critical section and make changes in a local copy of the shared variable. When the lock is available, then they update the shared variable with the local copy.
The other threads check the availability of locks. If it is not available, they will wait for it to be available again.
The other threads continuously check the availability of Lock.
The other threads cannot execute the critical section, until the lock is available.
Q.110 WNeed for Locks
Since now we have solved two problems using locks, can you tell us when we need locks?Select the correct statements that answer the above mentioned question.
When multiple threads are executing simultaneously
Whenever we are using threads
When multiple instructions need to be made atomic
When high priority threads don’t let low priority threads execute
Q.111 First thing in FizzzBuzz
After checking if the current value of the number is less than or equal to 'n' in the fizzbuzz example, what is the first thing that the threads do?Check if the condition is true
Increases the value of the count variable
Acquire the lock
Release the loc
Q.112 Scheduling in FizzBuzz Threads
In the FizzBuzz example, let’s suppose the scheduling algorithm used in scheduling the threads is the Round Robin algorithm. The order of scheduling is: T1, T2, T3 and T4, with such a time quantum which is enough to execute all the instructions in any of the methods associated with given threads.To make it more clear, following are the threads and their associated method:
T1: Executes Fizz method
T2: Executes Buzz method
T3: Executes FizzBuzz method
T4: Executes Number method
Now, following this scheduling of threads, can you tell us what will be the value of the shared count variable in the code used in lecture video, when the value of variable i becomes 5 and is about to schedule T1.
6
Q.113 What are the disadvantages of locks?
Contention: If one of the threads has acquired the lock, then all the other threads have to wait till the thread releases the lock. Other threads have to make continuous checks if the lock is available, which will waste CPU cycles.
Starvation: If a low priority thread has acquired the lock, then even if a high priority thread comes, it cannot execute its critical section, until the low priority thread releases the lock.
Deadlock: If thread T1 has acquired the lock on resource R1 and is waiting for resource R2 and thread T2 has acquired the lock on resource R2 and is waiting for resource R1, then they get in a deadlock and can never get out of this situation.
Debugging: It becomes difficult to debug the programs with locks in it.
All the above
Q.114 What is the disadvantage of the locks solution that the condition variables solution improves upon?
Contention: If one of the threads has acquired the lock, then all the other threads have to wait till the thread releases the lock. Other threads have to make continuous checks if the lock is available, which will waste CPU cycles.
Starvation: If a low priority thread has acquired the lock, then even if a high priority thread comes, it cannot execute its critical section, until the low priority thread releases the lock.
Deadlock: If thread T1 has acquired the lock on resource R1 and is waiting for resource R2 and thread T2 has acquired the lock on resource R2 and is waiting for resource R1, then they get in a deadlock and can never get out of this situation.
Debugging: It becomes difficult to debug the programs with locks in it.
All the above
Q.115 Threads in Conditional Variables
How does the conditional variable prevent the threads from continuously waiting for the thread?Select the correct statements that answer the above mentioned question.
The solution makes threads to check a condition and if that condition is true, then the threads go to sleep.
When the threads go to sleep, they execute the wait() operation. wait() operation adds it to the wait queue until this thread is notified that condition is false
When the thread using the lock releases it, then it notifies all the threads in the waiting queue.
The next thread to acquire the lock should be the last one to enter the waiting queue.
Q.116 What is the advantage of semaphores over the locks and conditional variables solution?
Deadlocks are not there in semaphores solution, whereas they are present in locks and conditional variables solution.
Debugging of locks and condition variables program is difficult, whereas the semaphores makes debugging easier
Locks and Condition Variables solution can be used to let only one thread execute the critical section, whereas the semaphores solution can be used to execute multiple threads in the critical section simultaneously.
None of above
Q.117 Acquire and Release
As we know that when a thread acquires a semaphore, then the value of semaphore gets decremented by 1 and when a thread releases a semaphore, then the value of semaphore gets incremented by 1.Now, let’s assume that the value of semaphore is initialized to 12 and in the course of execution of the process, semaphore is acquired 10 times and released 4 times. What is the minimum value possible for the semaphore?
Minimum = 6
Minimum = 4
Minimum = 2
Minimum = 8
Q.118 FizzBuzz and Race Condition
In the FizzBuzz problem explained in the lecture video, at many instances, all the four threads had the capability to execute the critical section simultaneously. How did the semaphores solution never run into race condition?Select the correct statement that answers the above mentioned question.
The semaphore is released immediately after the value is incremented.
The semaphore is acquired just before the condition is checked
At any instant of time, only one thread can execute the critical section and increment the value of a shared variable.
All these instructions (releasing and acquiring the lock) are wrapped inside a condition i.e. the critical section can only be executed if the shared variable’s value is less than n.
Q.119 Which of the following conditions is required for a deadlock to be possible?
Mutual exclusion
A process may hold allocated resources while awaiting assignment of other resources
All of the above
No resource can be forcibly removed from a process holding it
Q.120 The circular wait condition can be prevented by ____________
Using thread
Using pipes
Defining a linear ordering of resource types
All of the above
Q.121 Circular Wait and Hold & Wait
What is the difference between circular wait and hold and wait?Select the correct statements that answers the above mentioned question.
Circular Wait: There exists a circular chain between exactly two threads in such a way that each thread holds the resources that are needed by another thread in the chain.
Hold and Wait: Threads hold the resource with no intention to release it.
Circular wait: There exists a circular chain of threads in such a way that each thread holds the resources that are needed by another thread in the chain.
Hold and Wait: Threads hold the resource that has already been allocated to them and wait for the resource that they wish to acquire.
Q.122 A computer has six tape drives, with n processes competing for them. Each process may need two drives. What is the maximum value of n for the system to be deadlock free?
6
4
5
3
Q.123 Is Deadlock Avoided?
If the threads T1, T2, T3 and T4 want to acquire the lock on resources R1 and R2 in the following way:Yes
No
Q.124 Safe State
Given the following matrices for the allocated and maximum need of resources:Allocated Matrix:
| R1 | R2 | R3 | R4 | R5 | |
|---|---|---|---|---|---|
| PA | 1 | 0 | 2 | 1 | 1 |
| PB | 2 | 0 | 1 | 1 | 0 |
| PC | 1 | 1 | 0 | 1 | 1 |
| PD | 1 | 1 | 1 | 1 | 0 |
Maximum Need of Resources Matrix:
| R1 | R2 | R3 | R4 | R5 | |
|---|---|---|---|---|---|
| PA | 1 | 1 | 2 | 1 | 3 |
| PB | 2 | 2 | 2 | 1 | 0 |
| PC | 2 | 1 | 2 | 1 | 1 |
| PD | 1 | 1 | 2 | 2 | 0 |
Here, PA, PB, PC, PD are Processes A, B, C and D and R1, R2, R3, R4 and R5 are the resources. If the available resources are denoted by: R1 = 0, R2 = 0, R3 = X, R4 = 1, R5 = 1, then what is the smallest value of X, so that the given requirement will be satisfied and it will be in safe state.
1
Q.125 Request for more Resources
An operating system uses the Banker’s algorithm for deadlock avoidance when managing the allocation of three resource types X, Y, and Z to three processes P0, P1, and P2. The table given below presents the current system state. Here, the Allocation matrix shows the current number of resources of each type allocated to each process and the Maximum Need of Resources matrix shows the maximum number of resources of each type required by each process during its execution.Only REQ1 can be permitted.
Both REQ1 and REQ2 can be permitted.
Only REQ2 can be permitted
Neither REQ1 nor REQ2 can be permitted
Q.126 Select the correct statements for HDD and SSD
HDD consists of mechanical parts, whereas SSD uses NAND based flash memory to retrieve and write data.
HDD is faster in comparison to SSD in reading and writing data.
The smallest unit of HDD is sector and the smallest unit of SSD is page.
The data is read and written in blocks in both HDD and SSD.
Q.126 To Delete or To Truncate
A file is an abstraction. To define a file properly, we have to define operations that can be performed on the file. Operating system provides system calls to create, write, read, reposition, delete and truncate files. Deletion and Truncation operations have a thin line of difference between them. According to you, what is the difference between these operations?Select the correct statements that answer the above mentioned question.
Deletion involves removing all the attributes of a file, while truncation keeps all the attributes of a file.
Deletion releases the file space, while the truncation doesn’t.
Both the operations release the file space.
Deletion involves removing all the attributes of a file, while truncation keeps all the attributes of a file, except file length (which is set to zero).
Q.127 Removal from File Table
When do we remove the entry for a file from the open file table?When the file is closed by the process with most priority
When the file pointer moves to the beginning of the file
When the attribute file-open count becomes zero
When the file is closed by the process with least priority
Q.128 Locks in Storage Management
Which of the following is truly enforced lock and which operating system applies it?Advisory lock and it is applied by Windows
Mandatory lock and it is applied by Unix
Mandatory lock and it is applied by Windows
Advisory lock and it is applied by Unix
Q.129 Comparison between File and Directory
Select the correct statements for inode number of File and Directoryctime, atime and mtime are defined differently for File and Directory.
There is no difference in the inode numbers for file and directory.
For file, the type is defined as regular and for directory, it is defined as directory.
Inode number is only defined for a file.
Q.130 Match the following attributes of inode number with their correct description:
| Attribute | Description |
|---|---|
| 1. ctime | a. Time at which file/ directory was last modified |
| 2. atime | b. Time at which attributes of file/ directory was last changed |
| 3. mtime | c. Time at which file/ directory was last accessed |
1 - c, 2 - a, 3 - b
1 - a, 2 - b, 3 - c
1 - b, 2 - c, 3 - a
1 - b, 2 - a, 3 - c
Q.131 Linux Allocation System
Choose the correct statement about linked disk space allocation method.Access to the data is faster in comparison to contiguous allocation.
It allows both sequential as well as direct access.
There is no fragmentation and allows the file to grow dynamically over time.
None of above
Q.132 No External Fragmentation!
In a file allocation system, which of the following allocation scheme(s) can be used if no external fragmentation is allowed?I. Contiguous
II. Linked
III. Indexed
I and III only
II only
II and III only
III only
Q.133 Number of Requests
Suppose a disk has 201 cylinders, numbered from 0 to 200. At some time the disk arm is at cylinder 100, and there is a queue of disk access requests for cylinders 30, 85, 90, 100, 105, 110, 135 and 145. If Shortest-Seek Time First (SSTF) is being used for scheduling the disk access, the request for cylinder 90 is serviced after servicing ____________ number of requests.3
Q.134 Least Head Movement?
Which of the following disk scheduling policies results in the least amount of head movement.FCFS
Circular SCAN
Elevator
None of above
Q.135 Comparison between Algorithms
Suppose the following disk request sequence (track numbers) for a disk with 100 tracks is given: 45, 20, 90, 10, 50, 60, 80, 25, 70. Assume that the initial position of the R/W head is on track 50. The additional distance that will be traversed by the R/W head when the Shortest Seek Time First (SSTF) algorithm is used compared to the SCAN (Elevator) algorithm (assuming that SCAN algorithm moves towards 100 when it starts execution) is _________ tracks10
Q.136 Match the following
Suppose that a disk drive has 5000 cylinders numbered 0 to 4999. The drive is currently serving a request at cylinder 143. The queue of pending requests in FIFO order is- 86, 1470, 913, 1774, 948, 1509, 1022, 1750, 130. Starting from the current head position, what is the total distance that the disk arm moves to satisfy all the pending requests for each of the following disk scheduling algorithms?Match the disk scheduling algorithm with its corresponding distance moved by the arm.
| Scheduling Algorithm | Distance Moved |
|---|---|
| 1. FCFS | a. 1745 |
| 2. SSTF | b. 1917 |
| 3. SCAN | c. 3363 |
| 4. C-SCAN | d. 7081 |
| 5. C-LOOK | e. 9987 |
1 - d, 2 - a, 3 - b, 4 - c, 5 - e
1 - e, 2 - a, 3 - b, 4 - c, 5 - d
1 - d, 2 - a, 3 - b, 4 - e, 5 - c
1 - a, 2 - b, 3 - c, 4 - e, 5 - d